IT Security Policy
IT SECURITY POLICY
INDIAN INSTITUTE OF TECHNOLOGY, KHARAGPUR
1. PREAMBLE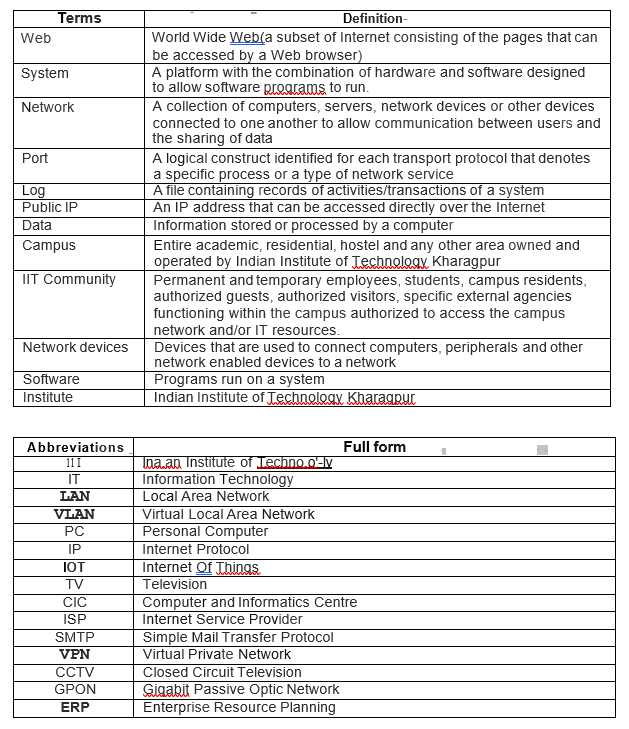
Attacks and security incidents constitute a risk to the academic mission of the Institute. The loss or corruption of data or unauthorized disclosure of information from research and instructional computers, student records, and financial systems could greatly hinder the legitimate activities of Institute faculty, staff, and students. The Institute also has a responsibility to reasonably secure its computers and networks from misuse. Failure to exercise due diligence may lead to liability for damage done by persons accessing the network facility from or through the institute.
Like many other organizations, Indian Institute of Technology Kharagpur has experienced a variety of security incidents of varying severity. Management of these incidents is the collective responsibility of the institute community. Failure to meet that responsibility could result in a tarnished reputation and also a potential liability.
The purpose of this policy is to establish guidelines, procedures, and requirements to ensure appropriate protection of the campus network and IT resources of the institute. The policy is intended to protect the integrity of campus network and IT resources of IIT Kharagpur and to mitigate the risks and losses associated with security threats to campus network and IT resources. In doing so, this policy also addresses the issues of confidentiality and integrity of personal and institute information.
The approved IT Security Policy is to be a public document and IIT community should be made aware of the policy and the requirement to abide by it. Failure to abide by any part of the security policy by a user may result in restrictions placed on the user's access to the campus network and IT resources as decided by the competent authority of the institute. The user will also be solely responsible and liable for any legal actions or any other implications arising out of failure to comply with any part of this policy.
2. SCOPE
This policy applies to all members of tne Institute community including all students, temporary and permanent employees, authorized consultants and visitors, authorized guests, campus residents of IIT Kharagpur, and any other persons not mentioned above but who are permitted and authorized to access the campus network and IT resources. This policy is also applicable to all users at extension centers and Guest Houses of IIT Kharagpur in different cities.
This policy also applies to all computers, networks, and data owned by and/or administered by the institute. For the purpose of this policy, the word "computer" includes all computing devices such as desktop PCs, servers, workstations, laptops, smart phones, IOT devices, smart devices and any such devices not mentioned above but are connected to Institute network.
All computers and network equipment owned by individuals are not subject to this policy as long as they are not connected to the institute network. If they are connected to the institute network, their operations are subject to this policy. All data owned by individuals are not subject to the policy as long as they are not stored on any computer owned or administered by the institute, or communicated over the institute network.
This policy is subject to revision and is to be re-evaluated by the institute as and when needed. All revisions are to be finally reviewed and approved by the competent authority.
3. ORGANIZATION OF THIS DOCUMENT
The policies specified in this document are divided into following parts:
a) General Usage Policies- identifies general usage policies of any Institute IT resources.
b) System Security Policies - applicable to all computer systems (as defined in Section 2)owned and/or administered by the Institute.
c) Network Security Policies - applicable to all active (for example switches, routers, access points etc.) and passive (for example wires/fibers, network points etc.) network components and accessories (for example power supplies etc.).
d) External Network Access Policies - applicable to all accesses to resources in the Internet from within IIT Kharagpur and accesses to the campus network from outside IIT Kharagpur.
e) Data Security Policies-applicable to all data stored on any system owned and administered by the institute.
f) Web Access Policies-applicable to web access from inside the Institute.
g) Mail Messaging Security Policies-applicable to mail messaging system of the institute.
h) Policies for Allocation and Management of Public IP-applicable to all systems with public IPs.
i) Physical Security Policies-applicable to critical IT resources of the institute.
j) IOT Security Policies-applicable to all IOT and smart (like TV, Fridge etc.) devices that are connected to the Institute network.
k) Security Assessment Policies-applicable to critical IT assets of the Institute.
I) Software Licensing and Usage Policies-applicable to all software running on computer systems owned or administered by the Institute or individually owned and connected to the Institute network.
4. GENERAL USAGE POLICIES
The policies herein guide the usage of any computer system (either owned or administered by the Institute or individually owned and connected to the institute network), Institute network, and any other part of the Institute IT resources by any user.
1. The Institute IT infrastructure is primarily for academic, administrative and reasonable personal use of the IIT Kharagpur community and should not be used by any user for any other purposes, which are in direct conflict with the role of the user without the explicit permission of the competent authority. Users may use the campus network and IT resources so long as such use:
a. does not violate any Institute policy, or the IT act or any other related law of the country
b. does not interfere with the performance of Institute duties or work of an academic or administrative nature of any other user
c. does not result in commercial gain or private profit other than that allowed by the Institute.
2. All users of the Institute computer systems and network resources have the responsibility to ensure overall security of the institute systems, and to behave in a
manner consistent with this security policy. Each user is responsible for understanding and complying with the IT Security Policy of the institute.
3. No systems or Institute network can be used by any user in any way to compromise the security of any other systems or networks anywhere, inside or outside the Institute.
4. No user shall send any information over the Institute network that may harm, threaten, intimidate, or harass others, or may otherwise be considered objectionable or illegal as per law. A user is solely responsible for any data stored by the user or sent by the user over the Institute network. A user will be solely liable for any legal action or any other implication arising out of such misuse. Under no circumstances shall the Institute be held responsible for any implication arising out of such actions of a user.
5. Installation and use of pirated software on Institute facilities or on individual machines connected to the Institute network is strictly prohibited. A user involved in use of any pirated software will be solely responsible and liable for any legal action or any other implication arising out of such use. Under no circumstances shall the Institute be held responsible for any implication arising out of such use of pirated software.
6. Any attempt to circumvent system security, guess others' passwords, or in any way gain unauthorized access to local or network resources is forbidden. Users shall not use another person's computing account, attempt to forge an account identity, or use a false account or e-mail address. A user involved in any such act will be solely responsible and liable for any legal action or any other implication arising out of such actions. Under no circumstances shall the Institute be held responsible for any implication arising out of such actions of users.
7. Any research and experimental activity on the Institute network that may hamper the operation of the network or compromise security of external or internal systems in any way is not permitted without explicit permission of competent authority of the institute.
8. Individuals aware of any breach of information system or network s curity, or compromise of computer security safeguards, must report such situations to the systems administrator or the departmental representative responsible for security in that area.
9. Users are strictly forbidden to use electronic mail and other network communications facilities to harass, offend, or annoy other users of the network, including interfering with their computing systems, software, or data. Sending of emails or messages masquerading as another person is not allowed. Users are not allowed to do any form of commercial advertising, or soliciting using institute email or network facility. Spamming is strictly disallowed. Subscribing to mailing lists outside the Institute is an individual's responsibility. A user will be solely responsible and liable for any legal action or any other implication arising out of any such emails or messages. Under no circumstances shall the Institute be held responsible for any implication arising out of such emails or messages.
10. Display of offensive materials (on computer screens, through digital posters, etc.) is strictly disallowed.
11. Any user of the Institute network is solely responsible for his/her opinion or usage of social media or any web site inside or outside of the Institute network, and will be solely liable for any legal action or any other implication arising out of such opinions and/or usage. Under no circumstances shall the Institute be held responsible for any implication arising out of such opinions and/or usage.
12. Users who are provided with facility to create their own web pages, both for generaJ access over the Internet and restricted access from within the Institute, are solely responsible for the contents of those web pages, and solely liable for any legal action
or any other implication arising out of such contents. Under no circ_umstances shall the Institute be held responsible for any implication arising out of these web pages.
5. SYSTEM SECURITY POLICIES
The policies herein apply to all computer systems (as defined in Section 2)owned and/or administered by the institute. The policies also apply to all such computer systems owned by individuals if they are connected to the institute network.
System Administration Policies
Any system (or a group of related systems, referred to collectively as a system hereinafter)owned or administered by the institute, or individually owned and connected to the institute network, must have a designated system administrator or an authorized person who will function as system administrator. For systems used by a single user (e.g. a faculty PC, student laptop), the administrator is to be that single user of the system.
A system administrator or the person functioning as system administrator has the following responsibilities for the system he/she administers:
1. Identify the set of users who are authorized to access the system.
2. Create and administer separate user accounts for each authorized user as per the user account and password policy specified later in this document.
3. Establish appropriate user privileges, monitor access and perform any other necessary security actions for the systems they administer.
4. Take reasonable precautions to safeguard against corruption, compromise or destruction of data in the system.
5. Prepare and maintain backup and recovery plans in case of any loss·of data due to security incidents for systems hosting critical data or services.
6. Take reasonable steps to maintain the privacy of user data stored in the system.
7. Take reasonable and appropriate steps to see that all hardware and software license agreements are faithfully executed on all systems.
8. Take reasonable steps to be aware of appropriate vulnerabilities, based on the operating system and services supported on the system
9. Ensure that operating systems and applications are kept current. Wherever appropriate, all the latest operating system and application patches must be applied on th_esystem regularly.
10. Whenever system security has been compromised, or even if there is a convincing reason to believe that it has been compromised, the involved system administrator must immediately either (a) reassign all relevant passwords, and force every password on the involved system to be changed at the time of the next log-in, or (b) take necessary steps to inform all users requesting them to change their passwords.
11. Ensure that any system configuration is done offline and the system is not connected to the network until it is at an appropriate level of security.
12. Ensure that only authorized persons install applications on a system.
13. Ensure that Security, Account, and System level logging is turned on when a server is set up.
14. Ensure that maintenance and service agreements with vendors are kept current wherever applicable.
15. Ensure that up-to-date anti-ma-lware software is installed in the system and updated regularly wherever applicable.
16. Ensure that all personal storage devices (USB disk, pen drive, diskettes etc.) and downloaded files are scanned before using them on the systems.
User Account and Password Policies
1. Each user should have a unique user ID in a system. System administrators or the person functioning as system administrator must be able to uniquely identify all users, including name, user ID, and other associated information. Certain system accounts such as "Administrator", "Backup Operator'' etc. are kept out of the purview of this rule.
2. The "Administrator" passwords to systems providing critical services such as mail etc. must be recorded and saved in a secure location for future reference.
3. Each user's profile must not be readable, writeable or executable by other users. Access to shared resources should be granted only as needed.
4. Accounts created to provide temporary services (for example, to a vendor for installation, a temporary visitor etc.) for a requested time period must be deactivated after the designated time period is over.
5. Accounts must be re-checked regularly to ensure that only valid accounts remain active.
6. All user accounts, where possible, must automatically have the associated privileges revoked after a certain period of inactivity.
7. All accounts must have assigned passwords.
8. Administrators and support staff must never request users to reveal their passwords.
9. Administrators and other support staff must not disclose users' identification and account passworc:ls to anyone.
10. It is recommended that users be asked to change passwords after initial login to a server.
11. Password files must be encrypted and passwords must not be stored in readable form in any files in a system, or anywhere outside the system where unauthorized persons might discover them.
12. A password must be immediately changed if it is suspected of being disclosed, or is known to have been disclosed to anyone besides the authorized user.
13. All vendor-supplied default passwords must be changed before any system is used.
Backup Policies
These policies apply to backup and restore of systems, which may be needed to recover any loss of data due to a security incident.
1. The system administrator or the person functioning as system administrator of a system must evaluate the need for taking system backups based on the nature of applications, services, and data hosted in the system. If backup is needed, the system administrator must decide the frequency and storage location of the backup based on the risk analysis of the system and the criticality of the data.
2. Systems with backup should be restorable, after any failure due to loss of data or compromise within a short period of time.
3. Backup media must be tested periodically to determine its effectiveness.
6. NETWORK SECURITY POLICIES
These policies apply to all active and passive network components like switches, routers, access points, fibers, wires, network points etc.
1. All network components in the institute are to be installed and administered by Computer and Informatics Center (CIC), except for any network extension made individually by faculty members or staff members inside residential quarters officially allotted to them by the institute. However, network components may be installed and administered by department/center/schools for special project and/or teaching needs with explicit written permission of CIC.
2. All departments/schools/centers or administrative/student bodies or any other entity, which have network components installed in their premises, must take reasonable and appropriate measures for physical safety of the components.
3. All departments/schools/centers or administrative/student bodies or any other entity which have network endpoints installed in their premises must take reasonable and appropriate measures to ensure that only authorized users access the institute network through the network endpoints.
4. Any change in the network installed and administered by CIC should be done by CIC or by CIC-authorized personnel in consultation with CIC.
5. Each managed switch/router must have a designated network administrator or a group of network administrators from CIC who will manage the switch/router. The administrator(s) is responsible for:
(a) Ensuring that only authorized personnel can access and configure the switch/router.
(b) Ensuring that all applicable security patches are installed regularly.
(c) Ensuring that if there is cause to believe that the switch/router is compromised, the issue is immediately reported to the appropriate higher authorities in CIC and action is taken to isolate the switch/router from the institute network if possible.
6. Access to the institute wireless network must be authenticated to ensure that only authorized users access the wireless network.
7. Sensitive applications must not be hosted on wireless subnets without adequate protection via encryption.
8. Sensitive data must not be transmitted over the wireless network without adequate protection via encryption.
9. Setting up of unsecured wireless systems on academic and hostel area is restricted. In residential areas, users are permitted to connect their personal wireless devices to the Institute network equipment, subject to adhering Institute IT security policy. However, they must disconnect their personal wireless device from the Institute network while connecting to any other ISP.
10. Software, computing or network devices within the Institute campus (owned by any department/section), and connected to the campus network, if declared end of support by the corresponding OEM, will be upgraded by the Institute at best effort basis to avoid any security risk arising out of it.
7. EXTERNAL NETWORK ACCESS POLICY
Other than web access, users of the network will access resources in the Internet for different reasons. Also, authorized users of the internal network may access it from outside IIT Kharagpur. The institute will follow the policies below for all access to any external network from within IIT Kharagpur and for all access to the internal IIT network from external sources.
1. All access via any protocol from the institute network to the Internet and from the Internet to the institute network must pass through a properly configured firewall centrally located in CIC.
2. The firewall will have one or more designated administrators.
3. The firewall must follow all policies specified in the System Security Policies section earlier in this document.
4. Institute will allow specific ports/services through the firewall for general users. Head, CIC will monitor this on periodic basis. Any other specific requirement due to academic/research/administrative/technical activity is to be treated as an exception and out of the purview of the general access policy. Such requirement is to be forwarded and permitted through the Departmental Heads/Deans to Head (CIC) for further actions.
5. Institute Firewall may block few ports/services if advised by the Institute authority/ Government agencies/lSPs/other competent agencies for security or any other administrative reasons. The firewall administrator upon approval of Head (CIC) will take necessary actions at the earliest to block these ports/services in the firewall as and when intimation is received from the above mentioned agencies/competent authorities.
6. Real time traffic log of the incoming and outgoing connections passing through the firewall should be maintained. This log is to be maintained for a period of 3 months.
7. CIC will be the custodian of firewall logs. Any request for sharing logs from any internal or external person or agency must be approved by the Director/Deputy Director/Registrar before the relevant parts of the logs can be shared.
8. The Institute firewall will have a built in intrusion prevention / protection system technology that examines network traffic flows to detect and prevent vulnerability exploits.
9. The firewall will authenticate all users accessing the Internet from the Institute network. Any exception to this policy should have the approval of the competent authority.
10. Access by authorized remote users to institute systems from any external networks to the institute network through firewall should use VPN or any other secure remote access software approved by Head (CIC).
11. Institute will have a limited number of VPN licenses for the activities mentioned in point number 5. The facility is to be provided to faculty members, staff and students on requirement basis for a specific period on approval of respective departmental head and Head (CIC).
12. All the external campuses of IIT Kharagpur in other cities may be connected to the internal network of the Institute and are to be treated as an extension of the Institute network if directed to do so by Director/Deputy Director.
13. The section 8 companies and similar entities related to the Institute are not to be directly connected to the Institute LAN. Whenever necessary these section 8 companies or any such similar entities are to be connected through the Institute firewall. Based on the requirement, these companies may be given permission to access specific Institute IT resources with the approval of the Director / Deputy Director.
14. Requests of live streaming of events inside the institute over the campus network for access from within and outside the institute are to be allowed when a written request is forwarded to Head (CIC) approved by the Director / Deputy Director I Registrar. In general, live streaming is to be restricted through the firewall.
15. It is strictly prohibited to connect other ISP networks (not obtained through CIC) to the Institute network without explicit consent from Head ( IC). When it is allowed, due to
research or operational needs, it should be the responsibility of the facility in-charge (preferably a faculty member) of that setup to completely firewall the external network from the Institute VLAN, both for inward and outward connections.
8. DATA SECURITY POLICIES
These policies apply to data that are deemed to be confidential or private.
1. Confidential data stored in an electronic format must be protected with strong passwords and stored on secured servers to protect against loss, theft, unauthorized access, and unauthorized disclosure.
2. Confidential data transmitted through a data network, must always be protected by using a secure connection method, such as VPN or SSH.
3. Confidential data must not be disclosed to parties without explicit management authorization and then only on a need-to-know basis.
4. Confidential data sent via fax, must be sent only to a previously established and used address or one that has been verified as being in a secured location.
5. Confidential data must be destroyed when no longer needed.
6. No systems on wireless subnets should store or transmit data of a sensitive nature such as credit card numbers; private student information, legal or attorney privileged data without adequate protection via encryption.
Privacy Policies
1. E-mail and other personal computer files/data/accounts of faculty members, staff members and students are in their personal domain and it is lnstitute's policy to respect privacy of such accounts.
2. The Institute, being the owner of the IT resources provided to its employ es and students with the primary objective of facilitating academic and administrative work, reserves the right to access personal account of any such user with the approval of the competent authority (Director/Deputy Director/Registrar) under the following circumstances:
(a) By order of a judicial or a.competent law enforcement authority
(b) On the basis of a complaint filed by any person or organization (either internal or external to the Institute) which alleges improper use of the account of a user for purposes such as, spamming, sending or forwarding harassing or abusive mails, or any other activity deemed to be in conflict with the usage policies defined in this document.
(c) On reasonable suspicion, supported by evidences such as download logs that the account stores and/or disseminates illegal material such as copyrighted or pirated material, hate mails, pornography, etc.
9. WEB ACCESS POLICIES
1. All users connected to Institute network will access web resources in the Internet through an Institute firewall(or a system with equivalent functionality) and will be subjected to the policies for web access implemented in the firewall.
2. The firewall will have one or more designated administrators.
3. The firewall should have the facility to block access to malicious sites and sites with objectionable contents.
4. The list of sites to which access will be blocked should be primarily decided based on
some reputed URL filtering software. In addition, institute may block other specific sites from time to time as needed. Institute may also allow access to some sites, which are blocked by the URL filtering software after carefully examining the need to do so. Head (CIC) will be the authority for deciding which sites to block or allow.
5. Irrespective of the list of sites blocked by the Institute firewall, the user will not attempt to access any web site that is illegal as per existing law. The user is solely responsible and liable for any legal action or any other implication arising out of any such illegal access. Under no circumstance shall the Institute be held responsible for any implication arising out of any such illegal access.
6. The user will not try to hack or otherwise tamper with any web site not directly owned or administered by the user. The user is solely responsible and liable for any legal action or any other implication arising out of any such activity. Under no circumstances shall the Institute be held responsible for any implication arising out of any such activity.
7. The user must not bypass the policies implemented in the firewall using any means. The user will be solely responsible and liable for any legal action or any other implication arising out of any such illegal access. Under no circumstance shall the Institute be held responsible for any implication arising out of any such illegal access.
8. Administrators of the firewall will maintain firewall logs to monitor web access activities.
9. Web access logs should be maintained for a period of 3 months.
10. MAIL MESSAGING SECURITY POLICY
1. All mail servers of the institute will have one or more designated administrators.
2. The mail servers must follow all policies specified in the System Security Policies section earlier in this document.
3. Mail administrator must ensure that all incoming mails in the SMTP gateway are scanned for viruses before they are delivered to the user mailboxes.
4. All usage and account management of the mail messaging system of the institute are to be governed by the IT Policy of the institute defined from time to time.
5. Mass mailing inside Institute mail-messaging system is restricted. In general, users are encouraged to use in internal notice board "APNA" for passing the information to all users. Mass mailing to group mailing lists covering all faculty mebers, all users, etc. may be done by Director / Deputy Director I Registrar / Deans I Chairman (ERP) / Head (CIC) or their authorized persons. Director / Deputy Director may permit few functionaries of the Institute to avail such facilities.
6. Users in no case should give out confidential information such as e-mail, ERP or system passwords, etc., in response to any email or otherwise. Institute should never ask for password or any other confidential information from the users over email. The individual account holders are to be personally held accountable in case of any misuse of their email accounts.
7. Users must avoid opening any mail or attachments arriving from unknown and/or suspicious sources or of otherwise suspicious nature without confirming the authenticity of the attachments.
8. Any attempt by the users to break into other users' email accounts is punishable. The punishment will be as deemed fit by the competent authority.
11. POLICIES FOR ALLOCATION AND MANAGEMENT OF PUBLIC IP
Most systems in the institute now use IP addresses from the private IP block. Public IP addresses are usually reserved for use by CIC on institute systems that need to be directly accessed from outside the institute (e.g., the institute web server). Machines with public IP addresses pose a security risk as they can be directly accessed from outside the institute and also because they can directly access any machine outside the institute. However, the need for allocation of public IP addresses sometimes arises due to various reasons such as faculty research needs, projects, administrative needs, etc. The following policies should guide the allocation of public IP by CIC:
1. Public IP addresses should be allocated only after very careful consideration of the actual need, and in rare cases when no other option is there. Allocation of public IP should be an exception, not a norm.
2. Only systems that require to be accessed directly from outside the institute should be considered for public IP allocation.
3. Wherever possible, applications/services/data that are required to be accessed from outside the institute should be hosted on a single system to reduce the number of systems with public IP addresses (e.g., hosting multiple web pages on the same web server).
4. Head(CIC) is the authority for allocation of public IP addresses.
5. Each machine assigned a public IP address must have a designated system administrator or an authorized person functioning as system administrator identified by the concerned faculty member or the head of the division using the system.
6. The designated system administrator or the person functioning as system administrator must ensure that the system always remains updated with the latest security patches, and must have a plan for regular vulnerability assessment of the system
7. The system administrator or the person functioning as system administrator must maintain logs to monitor access to the machine. The logs should be maintained for a minimum of 15 days. .
8. The system administrator or the person functioning as system administrator must monitor the system regularly and if there is any cause to believe that the security of the system has been compromised, the administrator should disconnect the system from the institute network and inform CIC immediately.
9. Wherever possible, the system should be physically located in CIC and placed in an appropriate security zone.
10. The faculty member or the head of the department I centre / school / section / unit using the system is finally responsible for any security attacks originating from this system to other systems.
12. PHYSICAL SECURITY
1. The Security section of IIT Kharagpur will look after the physical security of the campus that also includes the entire IT infrastructure.
2. All critical computing and network devices are to be kept in a place under lock and key or digital access control system or both. The respective departments or the hostel authorities are responsible for these resources and report to the Security section in case of any theft or any such eventuality.
3. The lnstitute's digital surveillance (CCTV) system may monitor the security aspects of the critical computing and network items in the campus as far as possible.
4. The responsibility of the GPON and other IT equipment in residential quarters provided by IIT Kharagpur will remain with the residents of the Institute quarters and any eventuality o"r theft must be reported to the Security section and CIC.
5. The responsibilities of the IT equipment like PC, Laptop, scanner, Printer and any other IT related devices provided by IIT Kharagpur to the users for their official use will remain with the concerned users. Any eventuality or theft must be reported to the Security section and the respective department / centre / school / section / unit.
13. IOT SECURITY POLICY
1. Required ports may be opened in the firewall for any IOT and smart devices for connecting to the Internet. It is the responsibility of the users to get the required port details to be opened from the manufacturers or the service providers. The exception to this policy is restrictive and can only be approved by Head (CIC).
2. Default passwords are not to be used in IOT devices. Users need to change the default passwords for the IOT devices and must maintain a strong login credential.
3. Device and software updates should be available and it is required that the devices be updated from time to time to eliminate any security risks.
4. Users must check the available features and disable any features that are not intended for use to reduce security risks.
14. SECURITY ASSESSMENT POLICY
1. The critical IT resources of the Institute should be protected from various security threats. Institute may conduct periodic vulnerability assessment and penetration testing or critical IT resources of the institute to minimize the risks for these critical assets.
2. Institute may also conduct other security assessment of critical assets and their compliance with any regulatory and or technological requirement from time·to time as needed.
15. SOFTWARE LICENSING AND USAGE POLICY
1. Any commercial (non-open source) software used by a user on a system connected to the campus network should have proper and valid license as applicable. Use of any software without a valid license, for which a license is necessary, is a serious offense as per law, and the user will be solely responsible and liable for any legal action or any other implication arising out of such illegal use of the software. Under no circumstances will the Institute be held responsible for any implication arising out of such illegal use.
2. For any educational, application and other type.s_,of software procured for academic, administrative and/or research purposes by the CIC, licenses will be managed by the CIC using suitable license· servers or otherwise to maintain a record of license distribution to the users.
3. For any educational, application and other types of software procured for academic, administrative and/or research purposes by any academic or administrative unit of the Institute, the corresponding unit shall maintain a record of license distribution to the users.
4. Individual users procuring software for research or personal use or any other purposes will have to adhere to the Institute IT security policy if the software is used on a computer connected to the Institute network. Such software is to be procured and used with valid licenses.
The security policy is to be reviewed and updated periodically by the institute subject to its own discretion and in accordance with the compliance to IT related laws of the country.
